Ad Tools For Mac
Explore the world of Mac. Check out MacBook Pro, iMac Pro, MacBook Air, iMac, and more. Visit the Apple site to learn, buy, and get support. Even Macs Need Antivirus Protection. The myth that Macs don’t suffer malware attacks has been. Self-Service Password Management Tool for Mac OS X Users. Organizations today increasingly deploy Mac devices. Due to this overall influx, the amount of Active Directory (AD) password reset requests for Mac devices has grown exponentially, as well. Thus, the IT teams of these organizations are forced to spend a lot of time handling repetitive. Particularly helpful on this front is a tool that can be used to move a local Mac users home folder to a network location and associate it with an Active Directory account.
As more Macs® are used within organizations, many IT admins are struggling with how to manage them. Generally, organizations have been using Microsoft® Active Directory® as their identity provider. But, limitations within AD have forced admins to ask whether there are Active Directory tools for Macs.

The short answer is yes, there are a variety of tools that can be used to bridge Mac authentication into Active Directory (AD). Traditionally, these solutions, called identity bridges or directory extension tools, were heavy duty, on-prem solutions that often required professional services to get up and running.
A new generation of tools can manage Mac systems in a way similar to how AD uses group policy objects (GPOs) for Windows® machines. We will talk about those later.
Why AD Tools for Macs?
The concept of Active Directory tools for Macs makes a great deal of sense because of the challenges that AD has with managing non-Windows user accounts and systems. Generally, AD can handle simple authentication functions across platforms like Macs. But, provisioning and deprovisioning accounts on non-Windows systems, running GPO-like policies, and securing Macs/Linux® systems can be challenging for Microsoft technologies, including Active Directory or even Azure® Active Directory.
For many IT organizations, the ability to extend identity and access management (IAM) to Mac, Linux, AWS®, G Suite™, Samba file servers / NAS appliances, and many other non-Windows platforms is critical. Their end users are using a wide range of IT resources, many of which are not Windows- or Azure-based. This freedom of choice is taking its toll on the IAM stances of many IT organizations.
The result is that IT organizations end up cementing their identity management infrastructure on-prem with their Active Directory instance, and several add-on tools, like an identity bridge, to connect to resources outside of AD. From a long-term perspective, this approach is not beneficial for growth, as studies show that cloud-forward companies grow almost 20% faster than their on-prem counterparts (SkyHigh).
Cloud IAM Tools for Macs
The good news is that a new generation of cloud-based Active Directory tools for Mac and other non-Windows platforms is taking over the IAM space. In fact, this approach can even replace Active Directory with a neutral cloud-based directory services infrastructure.
Now, this cloud-forward approach to an identity bridge is enabling IT admins to quickly and easily extend Active Directory to Mac and Linux systems. There is no on-prem infrastructure to manage and federating AD identities can be done easily in just a few minutes. A simple, lightweight agent on the Mac or Linux machine gives IT admins full control over user accounts as well as the system itself. This includes the ability to run cross-platform, GPO-like policies, execute ad hoc commands, or schedule tasks.
All of these capabilities and more are available from the Directory-as-a-Service® platform from JumpCloud®. You can use Directory-as-a-Service (DaaS) as an Active Directory tool for Macs, as well as a standalone cloud directory service. Learn more about DaaS by contacting us with your questions, or by checking out our blog or YouTube channel.
Where To Buy Mac Tools
Apple® has made huge inroads with Mac® systems over the last decade. Mac laptops and desktops have become a popular choice across organizations of all sizes in what was once a market dominated by Microsoft® Windows® systems. However, while Macs have become a common sight in the modern office, Microsoft Active Directory® (AD) has remained the identity provider.
Managing Macs with Active Directory presents challenges. Microsoft never designed AD to support Macs in the same way as Windows, nor are they interested in doing so. As the IT world shifts away from Windows to macOS® and Linux®, a significant number of IT admins want to know the best practices for integrating Macs with Active Directory.
Mac Management with Active Directory Falls Short
IT organizations have traditionally leveraged AD as their identity provider as well as their choice for managing Windows devices. AD offers a number of user and device management capabilities for Windows users and systems. However, the majority of these management capabilities aren’t available for Mac (or Linux). This presents a few major issues for IT admins.
The first issue is the lack of full control and management for macOS users. In large part, user management capabilities are limited to user authentication and password management. That means admins often have to implement third party add-ons to have the same level of control for Mac systems as they do for Windows endpoints in a pure AD environment. This not only adds a lot of complexity to user management, but also substantial added costs.
The other issue is the lack of device management capabilities for macOS systems. For example, one of the most powerful is AD’s Group Policy feature. Group Policy refers to a device management feature that enables IT admins to deploy commands and scripts to lock down aspects of the system itself. This could entail setting a screen lock timer or automatic OS updates. Microsoft calls these commands and scripts Group Policy Objects (GPOs).
While GPOs are certainly powerful tools, their effectiveness comes down to two factors. For one, they can only be applied to Windows systems. The other factor is systems must be directly bound to the AD domain. That doesn’t bode well for Macs.
The lack of GPOs for macOS endpoints in an AD environment is only a side effect of a larger problem. While it is easy to forget in the modern heterogeneous IT world, Windows and macOS are competing operating systems. Therefore, it is safe to assume that Microsoft will not be delivering system management capabilities for macOS systems on the same level as Windows endpoints any time soon.
Microsoft is not all that interested in providing support for a competing operating system like macOS. So if you have an organization that is deeply entrenched with AD, yet you’ve got a fleet of Macs to manage, the question has become, “What are the best practices for integrating Macs with Active Directory?”
Secure Remote Work
Get real-world tips to modernize your tech stack & improve remote security at our Sept. 29 webinar with a former General Electric CIO & a RedMonk analyst.
Options for Integrating Macs with Active Directory

Currently, there are three major options for integrating Macs with Active Directory.
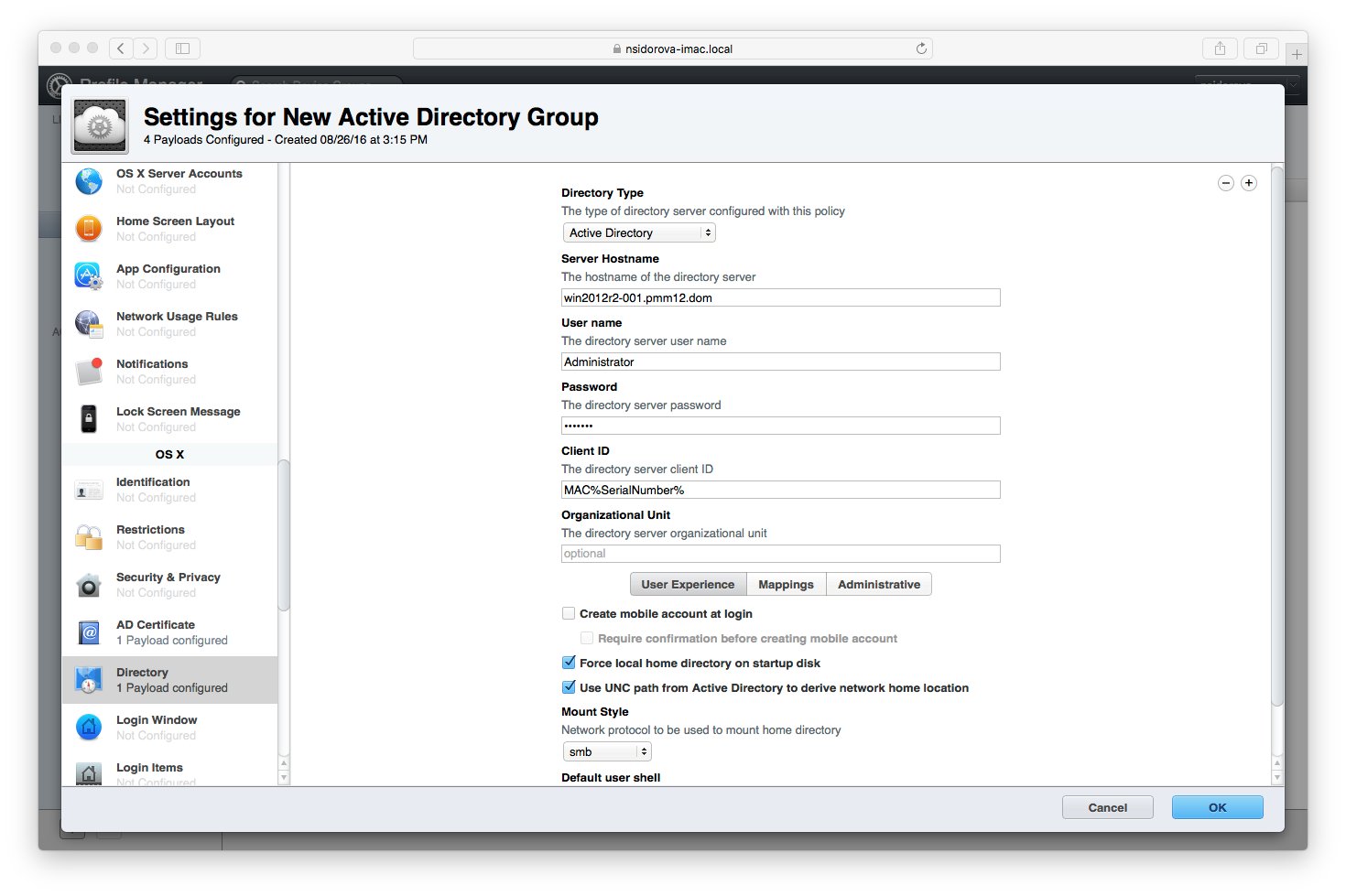
Option 1 is to manually connect Macs to AD. This can be done through some configurations and settings. It isn’t necessarily easy, nor scalable, but it can be done. What you don’t get is deep management capabilities as well as the concept of GPOs for Macs nor the full user management capabilities as you do with AD for Windows devices.
Option 2 is to leverage a legacy directory extension technology. These solutions are enterprise-caliber tools that integrate with the on-prem AD server. These solutions are often expensive and further solidify the identity management architecture on-prem, often as IT organizations are making the leap to the cloud.
Option 3 is to utilize a cloud identity bridge. The JumpCloud® Active Directory Integration that comes as part of Directory-as-a-Service® offers a particularly interesting example. This lightweight approach connects AD identities to virtually any resource that can’t be directly bound to the Active Directory domain. That can include not only Mac devices, but remote Windows machines, Linux servers at AWS, True Single Sign-On™ to web applications, WiFi authentication via RADIUS, and much more. This integration with AD federates to a cloud hosted directory service. As part of that directory service, IT admins can have full user and device control over their Mac fleet.
Mac Tools Parts List
So What is the Best Practice?
Best Mac Tools
Cloud identity bridges offer the greatest flexibility and allow an IT organization bound to AD to be more agile and adaptable as the modern office continues to evolve. AD Integration is unique in that it also offers GPO-like capabilities native to the functionality of Directory-as-a-Service. That means IT admins can set policies on Mac and Linux machines while AD remains the authoritative IdP.
Mac Tools Jobs
If you would like to know more about the best practices for integrating Macs with Active Directory, drop us a note. You can also sign up for an account and start extending AD today to your Mac fleet. Feel free to contact us if you have any questions.